Two-factor authentication (2FA)
Basic 2FA using TOTP
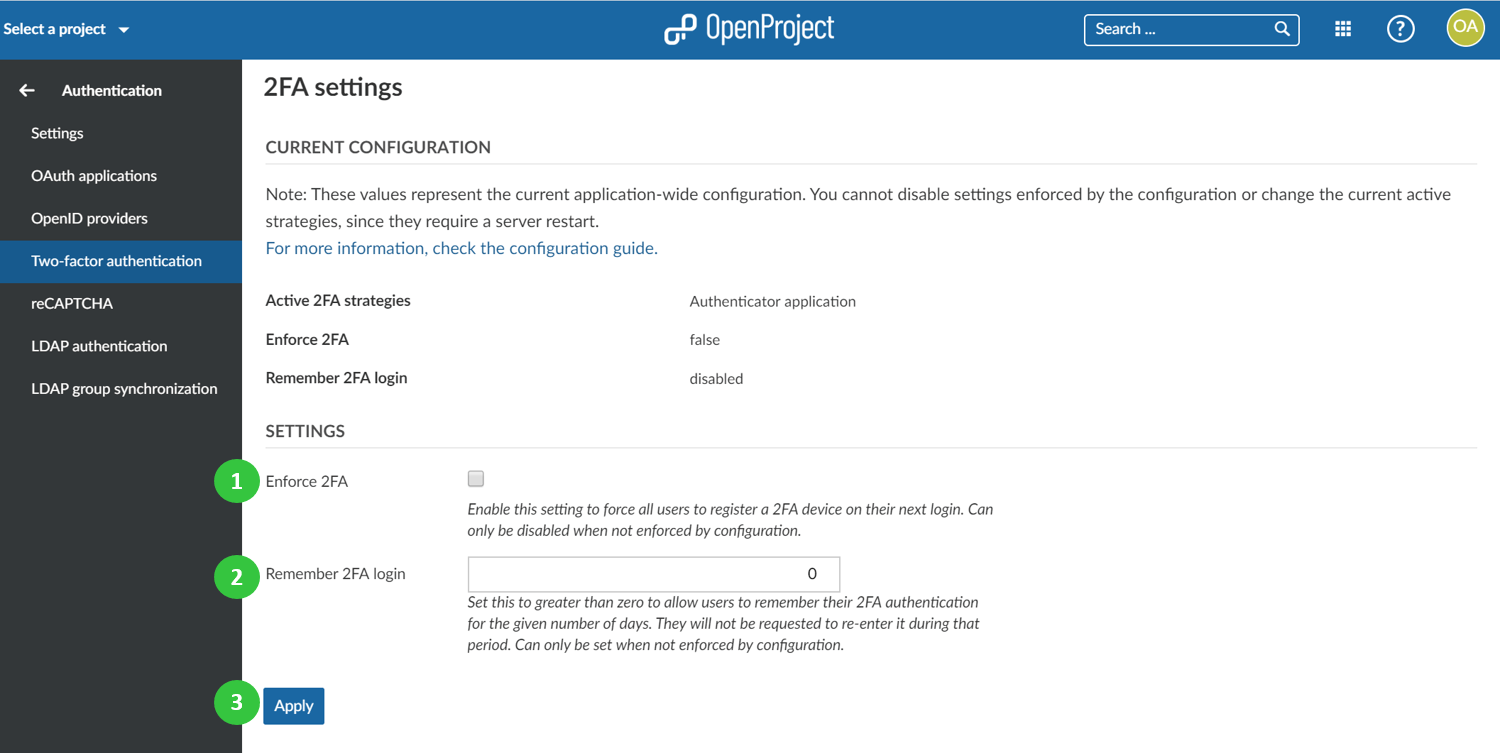
To activate and configure two-factor authentication for Nepenthes, navigate to -> Administration -> Authentication and choose -> two-factor authentication.
From the GUI you are able to configure the following options:
- Enforce 2FA (two-factor authentication) for every user. All users will be forced to register a 2FA device on their next login.
- Remember 2FA login for a given number of days, e.g. 30 days.
- Press the blue Apply button to save your changes.
Usually with another device device like a mobile phone or a tablet, you are able to use a TOTP Application in order to generate the token that is needed as an extra layer of security on top of your password. Here are some applications that work for Nepenthes 2FA.
Open Source andOTP (Android Device) in the Play Store
Open Source OTP Auth (Apple Devices) in the Apple Store
Google Authenticator
Microsoft Authenticator
Clock skew
TOTP operates on the principal that the second factor and the server handling the authentication process are roughly in sync. By default, the allowed clock skew (difference in seconds between client and server) is 30 seconds, which means that the server will accept time shifts of 30 seconds in the past and future, respectively.
If you are trying to register a new device and keep getting failures even though the code appears correct, time drift between the device and the server is most likely the reason for it.
Basic 2FA using WebAuthn
WebAuthn is a W3C standard for authentication on the web. It uses private-public key cryptography to verify the users identity. The private key is either secured on a hardware token or within the browser or a password manager.
WebAuthn is supported by most modern browsers and is therefore enabled by default in Nepenthes when 2FA is enabled.
Advanced 2FA using MessageBird, Amazon SNS
At the moment the advanced settings for improved security are only reachable by defining configuration variables.
Those methods are explained in the Two-factor authentication paragraph.